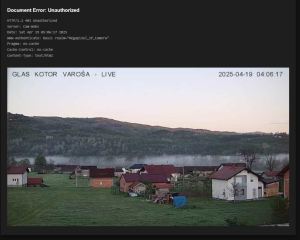
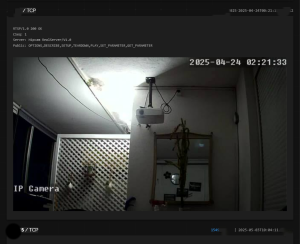
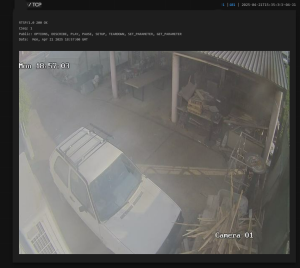
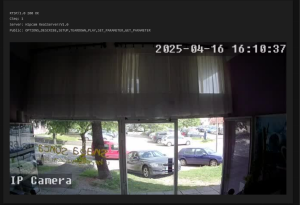
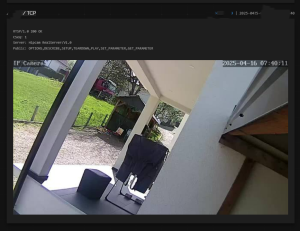
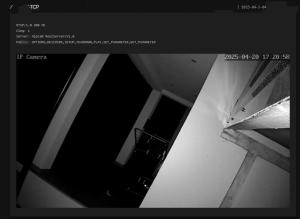
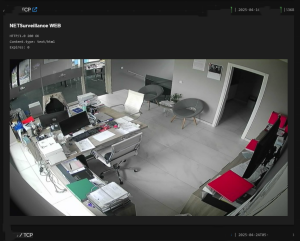
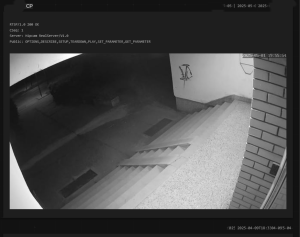
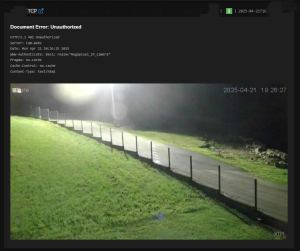
– All of these cameras have weak or default passwords
– Most unprotected cameras are in Sarajevo, Mostar, Zenica and Banja Luka
– At least 3,470 cameras installed without secured passwords came from the Chinese manufacturer “Hikvision”
BANJA LUKA – In Bosnia and Herzegovina, there are hundreds of thousands of surveillance cameras that record citizens day and night, and at least 5,660 of them transmit the footage directly to the internet without any protection or encryption.
Cameras are installed both on buildings and inside them, and can be found in state and local institutions, kindergartens, building entrances, as well as in many private companies, factories, family homes, and even children's bedrooms.
Research conducted by the CAPITAL media outlet revealed that thousands of surveillance cameras in Bosnia and Herzegovina (BiH) are virtually unprotected because they were left with default factory settings during installation—or have no password at all.
In collaboration with multiple IT experts and by using OSINT tools (Open Source Intelligence) available online, we discovered vulnerabilities in at least 5,560 cameras that can be accessed with little or no effort.
The most unprotected cameras are in Sarajevo (1,597), followed by Mostar (855), Zenica (536), Banja Luka (404), and Bijeljina (306). A review of the unsecured cameras list shows that almost every municipality and city in BiH has security flaws in its video surveillance systems.

An interesting finding is that at least 3,470 of these vulnerable cameras, left without strong passwords or with default factory settings, come from a single manufacturer—“Hikvision”, a Chinese company. This brand, along with “Dahua” (also Chinese), is among the most common in institutions and public spaces in BiH. According to Shodan, an internet tool, there are 852 vulnerable cameras by this manufacturer alone.
Chinese-imported cameras are the most common in BiH, which is unsurprising given their affordability compared to other brands.
However, what continues to be overlooked is the well-known fact that many surveillance cameras contain integrated elements that allow the manufacturer to access them at any time, raising serious security concerns, but manufacturers rejected those concerns.
Unsecured cameras are those left without a password or using default logins such as “admin/admin” or numbers from one to nine.
Some of these are installed in stores, cafes, residential buildings, and even company offices—and are open to the internet.
Anyone with minimal IT knowledge can access them—and even control them. These cameras are often included in so-called “open surveillance” networks, used by hackers and researchers for scanning.
Cybersecurity is not taken seriously
They also reveal IP addresses, which can easily lead to physical locations.
IT experts we worked with agree that cybersecurity is not taken seriously in BiH, and that privacy and data protection settings are often ignored, increasing the risks of abuse, illegal surveillance, and privacy violations.
The lack of responsibility regarding online security opens up a spectrum of risks, with more extreme scenarios, from planning attacks, including terrorism, theft, stalking and theft to espionage, and the illegal use or manipulation of recordings.

Experts warn that unprotected video streams may lead to various misuse of data, including voyeurism, espionage, and fake content creation, such as altering or deleting footage to mislead or spread disinformation.
Cybersecurity expert Nenad Borovčanin, who has years of experience in identifying vulnerabilities, says that video surveillance devices can be exploited by organized crime, botnet and sextortion groups, local criminals, or even curious individuals without malicious intent.
“Analyses have shown that there are unsecured cameras in BiH that are directly accessible over the internet. These include both private and public cameras. The general awareness of basic online protection is still underdeveloped, making these devices easy targets,” says Borovčanin.
Through vulnerable Camera to other devices
Weak video surveillance doesn't just affect privacy—it can become a gateway to an entire network.
“For example, a vulnerable camera can be a first step for an attacker to gain access to other devices on the same network, like personal computers or servers. There's also the risk of deleting or replacing footage, which can obstruct investigations,” Borovčanin adds.
When we talk about organized cybercrime, those involved often monitor poorly protected cameras for purposes such as espionage, data theft, and extortion.Networks of infected devices or botnets are remotely controlled by someone without the owner’s knowledge. In these cases, according to Borovčanin, the infected device appears and functions normally, but in the background it performs various operations commanded by the attacker.“These groups most commonly track inadequately secured cameras to recruit them into their botnet networks for DDoS attacks. A recent example is the ‘Mirai Botnet,’ malware created specifically for this purpose. There are also extortion groups focused on sexual content, known as ‘sextortion,’ whose main goal is to blackmail users by threatening to publish private videos on adult websites,” explains Borovčanin.
Surveillance cameras can also be misused by local criminals to monitor people, gather information about rooms in a building, and identify the routines of the occupants—looking for gaps in their schedule to exploit and steal property.Since identifying unprotected cameras does not require extensive technical knowledge, even individuals without malicious intent sometimes engage in spying on others and violating their privacy.
We’re being watched by 270,000 cameras
Our OSINT tools gave us insight into a huge amount of video surveillance data in Bosnia and Herzegovina. Using the Shodan tool, we found that there are over 270,000 surveillance cameras in BiH.
It’s important to note that this number changes in real time because Shodan constantly scans the internet.
We confirmed that it is relatively easy to find open cameras across BiH that show building entrances, cafés, garages, even rooms, as well as public spaces such as streets, squares, schools, institutions, and facilities under state and local government oversight.
All these cameras—and their routers and servers—have weak or default passwords.
The tools we used provided everything: from IP addresses to physical addresses, including photos and screenshots of footage from these locations, showing various offices, building and house entrances, balconies, as well as gatehouses of public universities, streets, yards, etc.They also showed that a large number of cameras are accessible even within institutions.
We emphasize that we did not access any of these cameras to avoid breaking the law; we only used publicly available screenshots and edited out anything that could reveal the locations or in any way compromise citizens’ privacy.
An IT consultant we worked with during the search for open cameras said there are still hundreds, perhaps thousands, of devices in public institutions that can be accessed without major obstacles.
He claims that at one point, there was a list of 5,000 cameras in public institutions across BiH that anyone could access. This led numerous experts to dedicate time to sending warnings to the institutions and improving security protocols.
“Additionally, we saw databases containing complete personal information about employees—from their addresses and personal ID numbers to bank account information and other highly sensitive data,” said one of our associates.
Incidents go under the radar
He adds that many incidents involving cameras have gone “under the radar,” meaning they were never reported to authorities—often because employees weren’t even aware the cameras had been compromised.
The Personal Data Protection Agency of BiH told CAPITAL that they continuously receive complaints from citizens about improperly installed video surveillance systems.
“In fact, this type of complaint dominates over other types of data processing complaints in recent years. Most reports involve illegally installed video surveillance systems by private individuals that cover public space or someone else’s property. We also constantly receive complaints about illegal surveillance systems installed by public institutions, legal entities, and other controllers who fail to comply with regulations regarding installation, data retention, and data handling,” the Agency said.
According to the current Law on Personal Data Protection, video surveillance constitutes data processing when used to monitor individuals. Since it involves systematic collection of personal data, the use of video surveillance must be prescribed, and data processing must be a necessary technical protection measure. The entity installing the surveillance is required to conduct a proper justification assessment for each individual camera.
“When processing personal data via video surveillance, everyone is obligated to ensure data security and to take all necessary technical and organizational measures. They must prevent unauthorized or accidental access, modification, destruction, loss, or unauthorized transfer of data, and avoid any other form of unlawful processing and misuse of data,” the Agency added.
Despite the evident seriousness of the problem, BiH still lacks centralized regulation and oversight over the installation of IP cameras in private or even certain public areas.
No clear protection or oversight
The rapid expansion of surveillance cameras, driven by uncontrolled imports and installations without a systemic approach, raises additional concerns about foreign influence and disinformation, experts warn.
All such equipment in BiH comes from foreign countries such as China, Japan, Taiwan, and others, and it’s possible that some have built-in security vulnerabilities.
Experts caution that some manufacturers pose a cybersecurity threat, including so-called “backdoor” access, which allows unauthorized access to video footage.
This enables foreign actors to monitor sensitive locations, collect intelligence, and prepare for the misuse of acquired information. Given BiH’s fragile political landscape, leaks and manipulation of footage could be used to destabilize the country or distort public opinion.
It’s worth noting that BiH has still not established a CERT (Computer Emergency Response Team), despite committing to this eight years ago. State institutions do not keep records, issue guidelines, or respond systematically to security incidents.
The Ministry of Security of BiH told us that in 2017, the Council of Ministers adopted a decision to establish a CERT for BiH institutions. Six years later, in 2023, changes were made to the Ministry’s job classification rulebook to create CERT-related positions—but evidently, nothing more has been done since. Only this year is the hiring of experts planned, but filling these positions will be challenging given the lack of interest among IT professionals to work for the state due to low wages compared to the private sector.
Interestingly, in their response to our questions, they said that monitoring the vulnerabilities of cameras is not within CERT’s jurisdiction.
“Monitoring vulnerabilities of cameras and IoT devices used in public and private spaces is not under the jurisdiction of CERT for BiH institutions. Responsibility for the protection, oversight, and control of cameras in private spaces lies with their owners, while the same responsibilities for cameras in public spaces rest with the so-called controllers, as defined by the Law on Personal Data Protection,” said the Ministry. They also stated that they are not aware of any recorded misuse of surveillance footage to date.
Video surveillance is a powerful tool
The EU’s CERT told us that almost all EU institutions and bodies have video surveillance in their premises—from small executive agencies with just a few CCTV cameras to institutions and bodies with offices in multiple member states managing hundreds of cameras.
“All EU institutions and bodies using CCTV have publicly available policies explaining what they do and why. Well-designed and selectively used surveillance systems are powerful tools for addressing security issues. Poorly designed systems create only a false sense of security while infringing on our individual privacy and other fundamental rights,” they stated.
They added that cameras can and should be used intelligently and should only target specifically identified security concerns, thereby minimizing the collection of irrelevant footage (data minimization).
This not only reduces intrusion into citizens’ personal data but also supports more effective use of video surveillance.
As digital infrastructure rapidly grows, BiH’s legal framework remains stagnant. There are no clear rules on user responsibility, equipment oversight, or data protection.
Experts call the situation concerning video surveillance in BiH “systemic negligence,” which can endanger citizens’ physical safety by opening channels for surveillance or more serious threats—even by individuals with basic knowledge and malicious intent.
Known vulnerabilities
Cameras from “Hikvision” (a Chinese company, Hangzhou Hikvision Digital Technology) and “Dahua” (Zhejiang Dahua Technology) have faced security vulnerabilities in recent years, along with accusations of illegal data collection and even industrial espionage.
According to British newspaper Politico and the U.S. Cybersecurity and Infrastructure Security Agency (CISA), a flaw in Hikvision’s products allows attackers to take full control of a device, potentially affecting over 100 million users. “Hikvision” acknowledged the vulnerability but denied involvement in data collection, claiming compliance with EU regulations. The company has been suspected of cooperating with Chinese authorities in mass surveillance and human rights violations in China.
As of late 2024, “Hikvision” had not completely fixed the issue in all affected models, leaving many devices vulnerable unless patched manually.
“Dahua” faced revelations of hidden backdoors and hardcoded credentials in its devices. For example, in 2017, vulnerabilities were found in Dahua cameras that allowed unauthorized retrieval of user passwords and full administrative access. An attacker exploiting these flaws could intercept video streams or repurpose the device as a launching point into the network. “Dahua” released firmware updates, but all devices that did not get passwords changed manually remain at risk.